You may have heard that “Blockchain has never been hacked, it’s the intermediaries (exchanges etc.) that are vulnerable”. This may have been true until a few years ago, but no longer. 2018 has seen not only a truly brutal market, but also several (!) successful 51% attacks of Blockchain.
Let’s take a look then, at what this attack is, how many times has it happened, and what are the possible solutions for it.
| At eToro you can trade 49 currency pairs, including several cryptocurrencies. Join eToro |
1. What is a majority attack?
51% attacks have several names. They are also called a majority attack, or a double-spending attack. As attackers are able to reorganise the chain, the hack is sometimes called “reorg” for short. In this article, these terms will be used interchangeably.
Most blockchain-technology works by sending data through the system that is only approved if the majority of miners get to a consensus that the transaction is valid. But what if someone gets hold of more than 50% of the networks mining power and tries to manipulate the system for his own needs? A 51% attack happens.
Here’s a short video on how it works:
Here’s what a majority attack allows the hacker to do:
- Reverse transactions that he sends while he’s in control. This has the potential to double-spend transactions that previously had already been seen in the blockchain, affecting all coins that share a history with the reversed transaction
- Reverse confirmations for any transaction that had previously been seen in the blockchain while he’s in control.
- Prevent some or all transactions from gaining any confirmations
- Prevent some or all other miners from mining any valid blocks
However, the attacker can’t:
- Reverse other people’s transactions without their cooperation (unless their coin history has been affected by a double-spend)
- Prevent transactions from being sent at all (they’ll show as 0/unconfirmed)
- Change the number of coins generated per block
- Create coins out of thin air
- Send coins that never belonged to him (source)
Interestingly, having a majority of the hashing power does not necessarily mean your intentions are bad. As a most notable example serves Ghash.io mining pool, which in July 2014 exceeded 51% of the overall mining power, resulting in a media and community storm. The company promised to keep its share of the network no higher than 39.99%.
| At eToro you can trade 49 currency pairs, including several cryptocurrencies. Join eToro |
2. Which Blockchains have been hacked?
51% hacks gained attention in the second half of 2016, when a group of hackers calling themselves the “ 51 Crew” attacked several clones of Ethereum, destroying Krypton, and severely damaging Shift. But this was just the beginning.
Fast-forward to 2018. Verge (XVG) has been hacked twice that year. In April 2018 a timestamp attack occurred (hackers exploited a weakness in code and were able to spoof timestamps, which made the intruder able to create new blocks using the same algorithm). Here’s an excellent in-depth explanation of the hack. The hack was dealt with by introducing a hard fork. Roughly 250,000 XVG has been stolen (but some claim the number may be as high as 3.9 million).
Only a few weeks later in May, the privacy coin has fallen victim to another attack. This time, roughly 35 million XVGs were lost, worth about $1.7 million at the time. Another coin, Monacoin has also been hit that May, suffering losses of around $90,000. The month also saw the biggest 51% attack to date, when Bitcoin Gold has been hacked for $18 million worth of tokens. You can find a very short analysis of the hack here.
Days later, in June 2018, ZenCash has lost over $550,000 in an attack. Soon after, Litecoin Cash has been attacked. However, in this case, the developers managed to warn exchanges in time, and the damage was minimal. One major silver lining of this attack was the created solution, called the Hive (explained later). Before the end of 2018, FLO Blockchain, Aurum Coin, and Vertcoin have been hacked in September, November, and December respectively.
2019 barely had a chance to start before a major cryptocurrency has been threatened. This time, Ethereum Classic was hit. The hack was first spotted by Coinbase engineers, and the team is currently dealing with the issue.
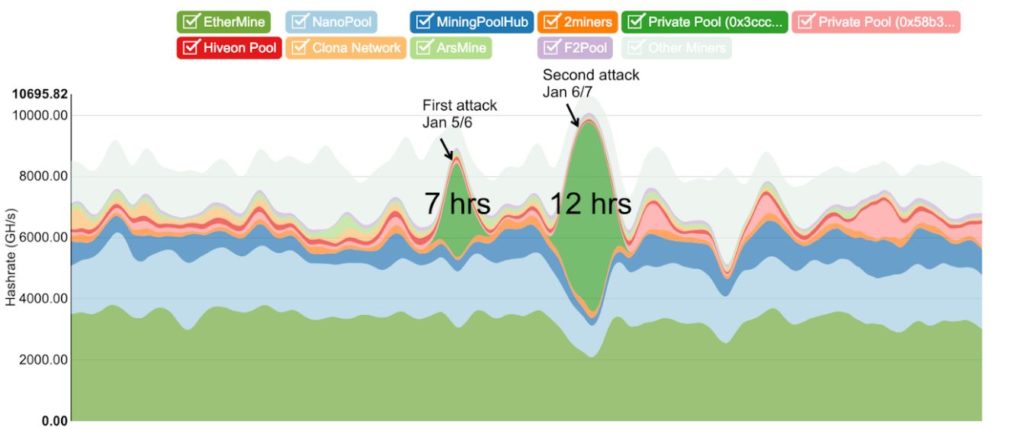
The whole hack took place between the 1st and the 7th January, and at least 219,500 ETC tokens have been stolen (worth almost $1m at the time of writing). A solution has not been found, but several recommendations have been made, and several priorities have been set by the team (source and details). It is the biggest cryptocurrency to fall under 51% to date (18th place, according to Coinmarketcap).
And keep in mind that the hacks mentioned here are only the ones we know of…
3. What makes some blockchains vulnerable?
In the original Nakamoto whitepaper, it is stated that the network should function in such a way that it is more profitable, to be honest, rather than steal coins. And the moment the profit/loss ratio tips in favour of the former, this incentive goes away.
There are two main conditions which make a blockchain especially susceptible to a 51% attack – having a Proof of Work (PoW) protocol and being a relatively small/young chain. Blockchains employing other consensus mechanisms, such as Proof of Stake, are safer when it comes to a double-spend attack. On the other hand, they have their own issues (e.g. Nothing at Stake issue within PoS). Newer chains are vulnerable here, but their small size actually protects them. If a coin has a low trading volume and is cheap, renting the hash power and attacking them is simply not profitable. Older, bigger chains make for big profit potential but are safer due to the sheer number of active nodes. As such, the biggest cryptocurrencies such as Bitcoin are untouchable, as this study shows and Antonopoulos argues in the short video below:
Another possible explanation for the high number of double spend attacks in 2018 is the bear market, which makes a 51% attack cheaper – falling prices translate into a significant idle hash rate that can be exploited and used to take over the network. It’s easy, as attackers can just buy up mining power without having to set up their own miners. Blockchains which utilise mining algorithms suited to other major blockchains are especially under threat here. Which is what ETC devs wrote in their post mortem post as a root cause of the recent hack: “In summary: ETC is still a relatively small PoW blockchain with a mining algorithm that is compatible with larger chains such as Ethereum so attackers can rent hash power on NiceHash to reorg the blockchain”.
| At eToro you can trade 49 currency pairs, including several cryptocurrencies. Join eToro |
If you’re curious how expensive it is to carry out a majority attack on a given cryptocurrency (check especially the ones you’ve invested in!), you can check out crypto 51, which shows the cost of 1 hour 51% attack on a given cryptocurrency while the Crypto Attack website shows (among others) attack profit and return ratio.
It has been suggested not to invest in any coin, which can be attacked for less than $100.000 a day (Emin Gün Sirer suggests 1 million USD as the lowest benchmark).
4. Solutions
A 100% certain method against a 51% attack doesn’t exist (yet, hopefully). And most of the suggested solutions or prevention methods are still being developed and debated. Some startups suggest new ways of mitigating attacks, while several companies which have already suffered under the majority attack propose a number of solutions of their own. In short, the solutions are few and hard to come by. Nevertheless, here’s the few we’ve found.
One of the main pieces of advice is to use alternative consensus mechanisms, and not to rely on Proof of Work (PoW). PoS, dPoS, and a hybrid of PoW and PoS are suggested as substitutes. PoS doesn’t rely on expensive hardware and therefore doesn’t need block rewards for miners. However, the community has debated the PoW vs PoS at length. Alternatively, you can launch your token on an established blockchain, such as Ethereum. Increasing the number of required confirmations also seems to work. The more confirmations needed, the longer the attacker has to wait to double spend, and the whole attack becomes more expensive. This was what the exchanges where Bitcoin Gold was stolen did. You can also make your coin profitable to mine, but that’s way easier to say that do. The God of Litecoin, Charlie Lee, suggests a solution of his own: merged mining. It addresses the weakness of the newer coins, as merged mining allows a miners pool to mine several cryptocurrencies at the same time, provided that they utilise the same mining algorithm. Another suggestion by Charlie Lee is to pay miners more; raising the reward for miners would make it more expensive to rent mining equipment. This solution, however, may be unaffordable for many cryptocurrencies.
As mentioned earlier, several companies and startups aim to improve the security of the network against chain reorganisation. Some companies learn from their experiences, such as Litecoin Cash which introduced the Hive: “Hive mining, an agent-based block minting priority contest, is proposed as a means to help secure a cryptocurrency blockchain. Hive mining increases network security over pure proof-of-work, providing protection from 51% attacks. Proof-of-work miners can continue mining as usual with no idle time, while a highly democratised alternative mining solution is available to those without specialised mining hardware. We introduce the idea of on-chain agents, worker bees, which act as virtual mining rigs with a negligible energy cost.” (source). ZenCash, also mentioned earlier, updated their protocol with a “delay function” (pdf here), where delayed blocks are penalised. This targets miners preparing for a majority attack by making the attack much more expensive to carry out. Although it seems like a logical idea, it still may have some weaknesses.
Startups are springing up, competing on their security. KOMODO, for example, has suggested notary nodes, which on one hand may add security, but at the same time grant significant power over the network to node maintainers. Some established companies are also taking preventive security steps, such as Dash, which has introduced a new protection mechanism called ChainLocks, based on LLMQs (Long Living Masternode Quorums).
| At eToro you can trade 49 currency pairs, including several cryptocurrencies. Join eToro |
5. Conclusion
There are some things to worry about when it comes to 51% attacks. Not only are they getting more frequent, but the solutions are often debatable. Furthermore, it pays to remember that after a majority attack the lost money is only the literal cost of the hack. The hack is always followed by negative press coverage, which in turn decreased the trust in the blockchain (and the project that launched it), and therefore investment as well. Price is often hit as well, with varying degrees of severity (reorg can kill a coin, or “only” decrease the price). Some coins end up being halted on some exchanges, and sometimes even delisted. All of these consequences make a 51% attack a catastrophic event for any blockchain project.
There may be some silver linings to all these troubles. Firstly, the number and scale of the attacks in 2018 and the recent ETC hack have made a lot more people pay attention. Secondly, major (let’s call them mainstream) cryptos like Bitcoin and Ethereum are quite safe (it would be too expensive to attack them), it is the newer coins that are under more threat. And although it brings little peace to smaller coins, there are steps you can take as an investor to mitigate your risk – remember to check how much it costs a day to attack the coins you’ve invested in. And once you know the cost, make a decision if you’re comfortable with that number. Finally, despite the fact that the fixes are not 100% certain yet, they are being developed. And the open-source nature of the Blockchain community will surely quicken new and exciting solutions.








